 Phishing scams are still among the most prolific cybercrime. Something as simple as having someone click on a link, attachment or image can start one of these attacks. Especially since sometimes the temptation to click on these links is very strong. Attackers can use simple strategies such as using your names in the subject for the email, or that of a family member or close friend.
Phishing scams are still among the most prolific cybercrime. Something as simple as having someone click on a link, attachment or image can start one of these attacks. Especially since sometimes the temptation to click on these links is very strong. Attackers can use simple strategies such as using your names in the subject for the email, or that of a family member or close friend.
For anyone, seeing their name in the subject of an email is alarming, to say the least. That’s why scammers write these emails in a way that makes you curious. They want you to click on the link to see what happens, that way you fall into their trap. What should we do in these cases? Next, we will explain what you should do to identify this kind of email and how to react to it.
Knowing its origin
A report published by the Statista website reveals that 11.69% of spam emails are born in China. This is the highest rate of generation of spam or malicious emails. However, the second place is even more alarming. With 9.04%, the second place where phishing is most used in the United States. This is because it is easier to work based on the payment of cryptocurrencies in these regions.
Since 2018, many scams of this style demand payment in cryptocurrencies. This change in tactics and the use of altcoins makes it more difficult to track payments. Thus, it is not easy to detect the attackers and that helps the market to proliferate.
How do you get our data?
A simple way to get mass emails is by hacking servers. If these servers have weak security protocols, it is not difficult for a hacker to get the data he needs. The violation of data in an email service or provider is also used.
Protecting yourself from phishing
 The main way to cut the risk of phishing is to limit the websites to which we provide our emails. Besides, password managers can help create more complex passwords. AlienVault, for instance, offers an excellent anti-phishing service. It allows you to identify these threats in the most efficient way possible.
The main way to cut the risk of phishing is to limit the websites to which we provide our emails. Besides, password managers can help create more complex passwords. AlienVault, for instance, offers an excellent anti-phishing service. It allows you to identify these threats in the most efficient way possible.
Another way to avoid falling into phishing is not to use your name or personal data. It is very common to see emails like janedoe1980@email.com: Here we see name, surname and year of birth. This is enough to find Facebook and undermine enough data to start with a phishing strategy.
Pay attention to the source
You should also learn to take a special look at the senders of emails. When criminals create email addresses they can select the display name. Thus, they can use a false address to attack the unawareness of their victims.
Other times they will use the name of the counterfeit organization to try to build more trust. No legitimate organization will communicate from an address ending @gmail.com. Each organization today will have its own email domain and business accounts. So, if the domain name matches the sender of the email, the message is probably legitimate. Besides, the best way to verify an organization’s domain name is by placing it in a search engine.
Yet, right now, anyone can buy a domain name. This complicates our previous point. Yet, there is another clue that provides info on the legitimacy of the mail. Although each domain must be unique, there are ways to create copycats of the originals. Creating an email with the domain “qoogle.com” will cause many people to fall for scams. The similarity between some letters lends itself for phishing and hackers can take advantage of it.
Spelling errors
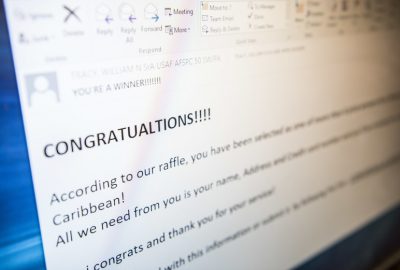 A good clue to know if an email is a scam is to check for bad spelling and grammar. Many of the scammers are not very good at writing. In fact, many of them do not speak English and don’t have much opportunities to learn the language. This makes it much easier to detect a scam.
A good clue to know if an email is a scam is to check for bad spelling and grammar. Many of the scammers are not very good at writing. In fact, many of them do not speak English and don’t have much opportunities to learn the language. This makes it much easier to detect a scam.
Using a spell checker will make all the words correct, but not in the correct context. Now, why don’t hackers use spell checkers or advisors to better write emails? Simple: These errors are part of a “filtering system”. This is because cybercriminals attack only the most credulous. The theory is that if someone ignores clues such as writing the message, it is more likely to fall for the scammer. People with a moderate level of knowledge are more difficult to cheat.
Going back to the spelling errors, once someone bites the hook, the scammer has to respond. Because to this, they prefer only those who can believe the rest of the scam.
Educate your staff about phishing
There is no way to be 100% safe online, but we can make it harder for cybercriminals. The main thing is to make your team know how to recognize the clues and identify phishing before it happens. Protecting your company from this security breaches is vital for its proper functioning. AlienVault is a unified platform designed to provide and guarantee a complete defense. Its Event Correlation program is effective against the most recent security threats.
If you want to know more about this topic and AlienVault, contact us. We offer you the best tools on the market and a team to help you on your way to a more efficient IT environment.



