SQL injection is one of the most common and oldest vulnerabilities that exist since the arrival of the digital era.
Despite their antiquity, today we still see them wreaking havoc, especially on less protected computers.
These types of attacks are responsible for controlling a database server behind a web application, avoiding authentication and authorization processes, and in the worst cases, the attacker can add, modify, and delete records from the database.
These vulnerabilities affect all types of websites as long as they use a SQL database such as MySQL, Oracle, SQL Server, and others.
In these situations, attackers illegally access confidential information including customer information, personal data, trade secrets, intellectual property and any other information stored on the server.
According to OWASP, SQL Injections rank as the number one threat to web application security.
How do these attacks happen?
Whoever carries out these attacks searches for vulnerable user entries within the web page or app.
Those pages or applications that present this vulnerability allow the attacker to create incoming content (also known as malicious loading) and, once sent, its executed in the database.
The consequences of SQL attacks, depending on the case, can be very serious, these include
- Search for other users’ credentials in the database, which leads to impersonation and, as the case may be, to complete and privileged administration of the data stored on the server
- Select, modify and add data to the database
Delete data from the database, this can affect the availability of the web page or web application, even if there is a backup of the information, until the admin performs a complete restoration.
Because some servers give access to the operating system through the database server, the attacker(s) can implement this attack as the initial vector and then proceed to attack the internal network behind a firewall.
Example of SQL injection
Below, you will see how an attacker will take advantage of this vulnerability by authenticating himself as an administrator.
In addition, you should know that this script runs a pseudocode in a web server using a simple case of authentication by username and password, where the database used as an example has a table named with the following columns: username and password
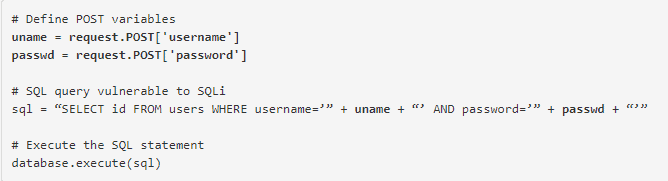
These fields are vulnerable to SQL injections, allowing the attacker to alter the SQL instruction executed by the server.
For example, you could add a simple quotation mark and set the field to: passwd
![]()
As a result, the server executes the following SQL query
![]()
This instruction returns the first one in the table regardless of which “and” they are.
The first user of a database is usually the database administrator. Therefore, the attacker not only skips authentication, but also gets administration privileges in the process.
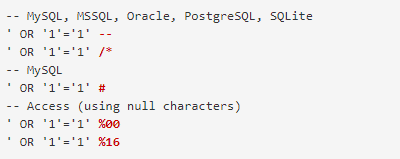
In addition, the attacker has the power to comment on the rest of the SQL statement to control (further) the SQL query: OR 1=1WHEREidusersusernamepasswordid
SQL injection attacks in 2020: Freepik and Flaticon
SQL injection attacks are quite common despite the technologies available today.
Any company, business, website or web application can be a victim of these attacks regardless of its size or importance in the market, as we will see in the following example:
Freepik and Falticon, companies in charge of offering an enormous amount of resources to the graphic world, were recent victims of this type of attack.
Both companies saw the data of 8.3 million users compromised, which included information from their e-mails and passwords.
Most of the users actually affected by this attack had weak or easily deciphered passwords.
This error on the part of users is, unfortunately, more common than it should be.
If you want to know how to create stronger and more secure passwords, we recommend reading our tips for strengthening your passwords.
On the part of the companies involved, this error did not escalate because they managed to identify themselves in time.
What measures were implemented?
The measures implemented included canceling the passwords that were compromised and sending an email informing users of the situation.
users changed their password without any problem, likewise, in the mail, the company advised them to change any other password similar or equal to the one used in their Freepik or Flaticon account.
After this attack, the company took a new direction in terms of the security of its web platforms and now performs regular checks to see if filtered addresses and passwords are being used to notify the account owner and follow the proper procedure.
Find out how and why you should implement identity-based access controls so you do not become a victim of this type of incident.
6 steps recommended by Acunetix to prevent SQL attacks
Acunetix is a cybersecurity tool specially designed to solve the vulnerabilities of web pages or applications.
It offers a specialized scanner that detects SQL vulnerabilities instantly and allows IT teams to find effective and lasting solutions in a matter of minutes.
Avoiding SQL injections is not easy, since they depend on several factors such as the SQLi vulnerability subtype, the SQL database engine, and the programming language.
However, Acunetix recommends these six steps to reduce the chances of being a victim of this type of attack.
Step 1: Train and maintain awareness
Everyone involved in the creation of the web application should be aware of the risks associated with these vulnerabilities.
Thus, providing information and training to all personnel involved in these processes is recommended.
Step 2: Do not trust any user input
Any user input using SQL authentication represents a potential risk of SQL injection.
Therefore, Acunetix recommends treating all user input as if it is untrustworthy.
Step 3: Use white lists, not blacklists
It is advisable to filter user entries using white lists instead of blacklists.
A skilled attacker knows how to evade detection by the blacklist.
If possible, you should filter each user’s entries using only strict white lists.
Step 4: Use the latest technologies
Many older web development technologies do not have SQLi protection.
It uses the most recent version of the development environment and language, as well as the technologies associated with them.
For example, you should use PDO instead of MySQLi in the PHP language.
Step 5: Use verified mechanisms
Trying to build SQLi protection from scratch should be avoided.
Most modern development technologies offer you protection mechanisms against SQLi attacks.
For example, it is better to use parameterized queries or stored procedures that ensure their security.
Step 6: Regular scans (with Acunetix)
The main source of SQL injections are the developers or through external libraries/modules/software.
What you can do is to keep a constant scanning using certified and professional tools such as Acunetix.
Finally, you can follow this link to learn how to protect your website with Acunetix.
Acunetix + GB Advisors: The best combination, the only solution
Give your company and its customers the security they deserve with Acunetix, from today.
You can purchase your free Acunetix demo with us, just contact us and ask for it.
At GB Advisors, we offer you the ITSM solutions you require.
We offer complete and personalized assistance through the installation, configuration, and implementation processes of this and many other tools.



