The concept of social engineering regarding information security directly refers to data theft by the manipulation of end users 1.. Thus, the risks and threats of social engineering usually start in a casual, innocent contact, via social networks or Internet; but they usually end up in the attempt of breaking the digital security of targeted companies.
The concept of social engineering regarding information security directly refers to data theft by the manipulation of end users 1.. Thus, the risks and threats of social engineering usually start in a casual, innocent contact, via social networks or Internet; but they usually end up in the attempt of breaking the digital security of targeted companies.
For this reason, you need to raise awareness campaigns among your employees to identify and mitigate the risks and threats of social engineering; and transform them into a defensive line of attack to expel possible intrusions to your sensitive data. Let’s discover how them in depth.
Types of Social Engineering
Basically, they are two known types of social engineering. The first type bases its techniques on human interaction to exploit vulnerabilities (or weaknesses) and getting access to the sensitive data through them. The second type bases on our interactions with the Internet through computing devices. But let’s go deeper in each of them.
1. Social engineering based on people
 Those who take advantage on social engineering based on people are particularly tenacious. Thanks to this attribute, they know how to exploit and manipulate human emotions to fulfil their purpose.
Those who take advantage on social engineering based on people are particularly tenacious. Thanks to this attribute, they know how to exploit and manipulate human emotions to fulfil their purpose.
They understand and apply psychological and motivational theories to move complex feelings (compassion; love; fear; curiosity; need to belong to a group; need for protection; etc.) and/or primary needs (sex; hunger; sleep; thirst; etc.) to make the targets to lower their defenses; and deliver the information they want without even realizing it. Same, they know that all humans basically share the same fears; weaknesses and needs; and all of them get inevitably reflected in our interactions on the web.
So, they take advantage of all these aspects to impersonate a co-worker; boss; or some authority to offer products or services oriented to attack our most precious assets.
2. Social engineering based on web interactions
Following, the most common use of social engineering based on web interactions is phishing or whaling (identity theft). As sophisticated as social engineering based on people; this other variant uses emails and fraudulent websites to obtain sensitive data.
 Los ingenieros sociales, transformados en piratas informáticos, logran imitar muy bien las características institucionales de las comunicaciones internas. Suelen ser tan bien acabadas que pasan los filtros iniciales; y engañan por completo a los usuarios finales.
Los ingenieros sociales, transformados en piratas informáticos, logran imitar muy bien las características institucionales de las comunicaciones internas. Suelen ser tan bien acabadas que pasan los filtros iniciales; y engañan por completo a los usuarios finales.
Social engineers, now wearing grey or black hats, successfully copy the institutional communication features. And they are so good at it that usually pass the initial filters to completely deceive the final users.
In other words, social engineering based on web interactions aim at undermining the digital security of enterprises; and they usually accomplish their objective converting the attempts in particularly damaging and successful attacks.
Social Engineering – Methodology
Regardless the applied type of social engineering, the methodology goes like this:
-
Approach phase
In this first stage, the approach aims to win the target’s trust. Generally, the attacker uses social engineering allows the target to control the communication because like this, it becomes easier to detect primary weaknesses.
-
Alert phase
Following, the attacker presents a range of options to observe and measure the target’s response under pressure. At this stage, the attacker’s degree of interaction changes from passive to active to send loose propositions here and there; all specially designed to assure the trust initially established.
-
Distraction phase
Finally at this phase; the attackers have consolidated much of the confidence they need to get the sensitive data. The target feels at ease and lowers its defenses. In parallel, the attacker practically dominates the all interaction. However, the attacker advances carefully towards the objective so to not prevent the target to re-raise the alarms.
 With this in mind, the attackers reassures the targets with promises or confidence phrases that end by putting their barriers down. Then, as a natural part of the interaction; the targets finally deliver their sensitive data such as passwords to access private accounts or ‘voluntarily’ giving their security numbers of their credit cards.
With this in mind, the attackers reassures the targets with promises or confidence phrases that end by putting their barriers down. Then, as a natural part of the interaction; the targets finally deliver their sensitive data such as passwords to access private accounts or ‘voluntarily’ giving their security numbers of their credit cards.
This methodology has proven to be extremely powerful because it undermines the defenses of the targeted companies and individuals who, in addition to losing money and their privacy; also lose confidence of their abilities to protect themselves from security attacks.
In short, the victims of any form of social engineering feel vulnerable and upset, and in this sea of emotions; they miss the all picture of what they have had passed through and blame themselves on their loss. However, there’s always a solution.
What solutions exist to catch up the risks and threats of social engineering?
The most effective solution to repel on time the threats of social engineering resides in the combination of automated tools with best practices to help you train your staff in early threat detection.
In more technical terms, repel threats of social engineering demands the use of reverse engineering. As the statement explains, it is nothing but following the reverse path to fully comprehend the different phases of a process.
So, in order to counteract the threats of social engineering, reverse engineering goes like this:
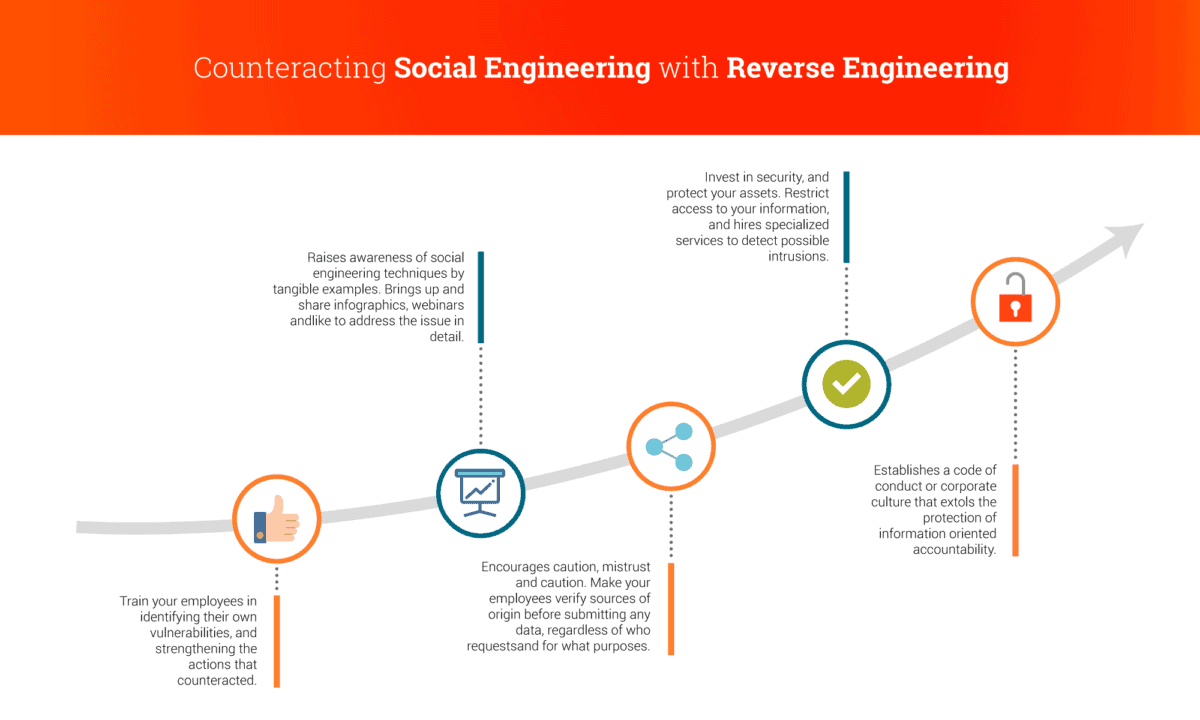
Hunt the hunter: Infringe the principles of social engineering
We have mentioned it on other occasions, but yes, we bet on emphasize it again: Soldiers are the best weapon in every war. Arm your soldiers with these best practices:
-
- Relevance. No serious company ask for passwords, user names, Social Security numbers or other similar data.
- Urgency. Messages such “Respond this communication within the next X hours, otherwise, you will lose all the information of your account” generally are aimed to destabilize the users to force them to reveal sensitive data.
- Customization. Your service providers know your name and your employees, therefore, an email without your names on them are highly suspicious.
- Control. Avoid surrendering to your impulses and emotions. Feelings like cooperation; praise; intimidation; persuasion; ingratiation or similar will be the means to get what they need from you or your employees.
Scope of social engineering
Hackers will use social engineering to track all your interactions within the web to put their hands on your sensitive data. And do you know what is a goldmine for their purposes? Yes, you’ve guessed: Your mobile devices.
As they enable the option to save passwords and relevant information it’s of utmost importance that you extend to your mobile devices all your protective measures. And this is where we can serve you.
Discover here with us the options we have to protect your sensitive data from the tentacles of social engineering, their risks and threats.