 In our most recent post: “10 Common Practices that Exposes You to System Security Breaches”; we made reference to the risk we expose to when opening attachment in our emails. Few days later, ransomware WannaCry showed up into scene to illustrate our point: Even our reliable sources may expose us to system vulnerabilities. As consequence; we must always keep on guard and leverage our digital security measures in our networks.
In our most recent post: “10 Common Practices that Exposes You to System Security Breaches”; we made reference to the risk we expose to when opening attachment in our emails. Few days later, ransomware WannaCry showed up into scene to illustrate our point: Even our reliable sources may expose us to system vulnerabilities. As consequence; we must always keep on guard and leverage our digital security measures in our networks.
Of course, this translates into considerable loss in terms of money: At release, projections sum up to USD 32,000.001. However, the highests costs for enterprises go beyond to strictly material damages.
The recent attack of the ransomware WannaCry against thousands of enterprises around the world; is another reason to always keep an eye on our systems against ransomware. In this link we found pretty much what we need to know about ransomware WannaCry:
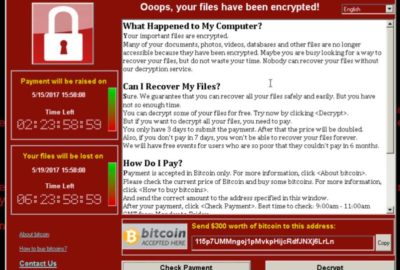
“Ransomware like WannaCry works by encrypting most or even all of the files on a user’s computer. Then, the software demands that a ransom be paid in order to have the files decrypted. In the case of WannaCry specifically, the software demands that the victim pays a ransom of $300 in bitcoins at the time of infection. If the user doesn’t pay the ransom without three days, the amount doubles to $600. After seven days without payment, WannaCry will delete all of the encrypted files and all data will be lost.”
Additionally; it’s more than enough that ransomware WannyCry hits just one device on your networks to potentially infect and damage every other device on it.
How ransomware WannaCry works?
At programming level, experts explain that ransomware WannaCry exploits a remote command execution vulnerability through protocol SMB (MS17-010). Then, ransomware WannaCry spreads out to the rest of the devices using OS Windows attached to the same network.
 However, as every vulnerability; ransomware WannaCry needs in the first place to make its way through the local networks from any device. Especifically, it requires somebody to open a gate from his or her email: Ransomware wannacry goes unnoticed in any attached file, and ‘activates’ when finding any valuable data to ask for rescue.
However, as every vulnerability; ransomware WannaCry needs in the first place to make its way through the local networks from any device. Especifically, it requires somebody to open a gate from his or her email: Ransomware wannacry goes unnoticed in any attached file, and ‘activates’ when finding any valuable data to ask for rescue.
Now, due that the recipient usually trusts in the remitent/source; and carelessly opens the attachments; this scam is as dangerous as efficient. Additionally, it also uses different ways of infection2:
Its «ability» consists in remotely blocking the access to specific files in the PC by encrypting them and then; changing their extensions from as for expample: Maps.doc to Mapas.wanacry. Its most common source or vehicle of infections is the email. (…) One out of three infections occurs by opening an infected link from emails; 28% by opening an infected attachment from emails; and a quarter by visiting unsecure pages.
How can we disable the ransomware WannaCry from an infected network?
According to Microsoft, we already count with solutions to remedy this system vulnerability. It’s a patch available in the last cumulative upgrades in the last months, whose last alert was released on March 14, 2017:
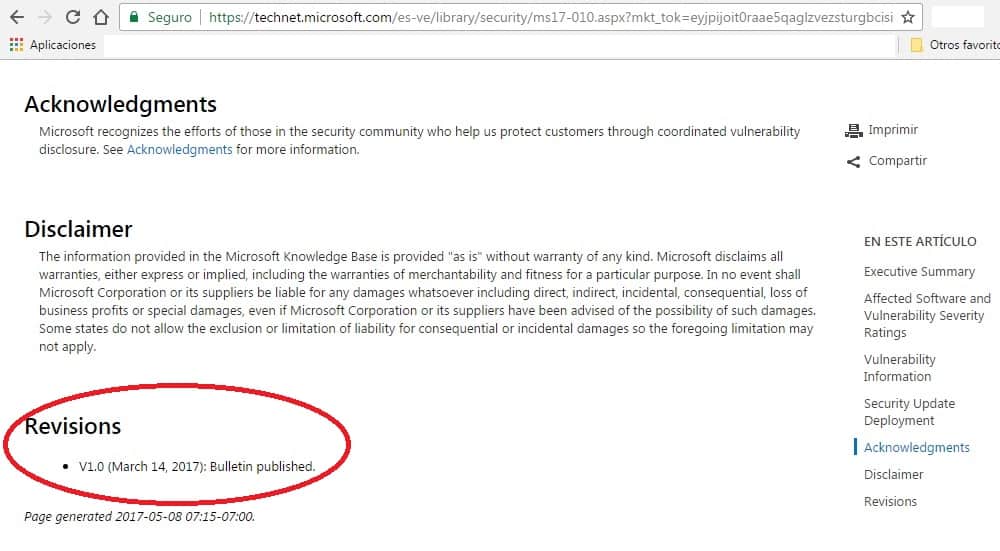
Also, on May 15, 2017; Microsoft released patches called KB4012598 for Windows 8, XP, Vista, Server 2008 and Server 2003 to protect against “Wanna Cry” ransomware.
Additionally, we also count on the solution given by Marcus Hutchins and Darien Huss; the ‘accidental heroes’ from this story who found the way to make it through this vulnerability in a very clever way… and temporary, though.
As we already count on solutions, are we completely save from suffering an attack of this ransomware?
 This threat is still spreading on because there are some variations of ransomware WannaCry. Some of our partners have expressed their possition about this attack. To that effect, we quote AlienVault:
This threat is still spreading on because there are some variations of ransomware WannaCry. Some of our partners have expressed their possition about this attack. To that effect, we quote AlienVault:
As of early this morning (May 12th, 2017), the AlienVault Labs team is seeing reports of a wave of infections using a ransomware variant called “WannaCry” that is being spread by a worm component that leverages a Windows-based vulnerability.
On the other hand, our partner Trend Micro also speaks about this attack:
Since these are specific exploits to Microsoft products and platforms, customers are always strongly advised to have current and officially supported versions of Microsoft products and platforms deployed with the latest security patches installed.
However, we recognize that many enterprise and business customers have legacy platforms still in production for various reasons. Fortunately, Trend Micro already has some solutions available that provide some level of protection.
Same, Tenable spoke about this issue on these terms:
Tenable.io™ customers can easily create a scan to find hosts that are susceptible to the WannaCry malware. (…)
Most ransomware attacks are caused by exploits of known vulnerabilities that remain unpatched on systems. This is especially true for systems running outdated and unsupported operating systems.
Why ransomware WannaCry spread out so fast?
The answer is pretty simple and basically remains in the inconsistency of keeping best practices regarding security. However, education and sensibilization as technology users is the first step to improve security in our workplaces.
On the other hand, if we take its camouflage capability, and add it up to the regular practices of disregarding the security alerts and lacking the upgrades for OS; we give more space to vulnerabilities to attack our networks and systems. And there they reside the truly security breaches we expose to without notice.
 Last but not least, we notice a pattern: According to the experts; many of the companies with the ransomware WannaCry operate with outdated/cracked OS Windows versions. Same; those who count on the most recent versions usually neglect patches and upgrades.
Last but not least, we notice a pattern: According to the experts; many of the companies with the ransomware WannaCry operate with outdated/cracked OS Windows versions. Same; those who count on the most recent versions usually neglect patches and upgrades.
Let’s see now what can we do to prevent security breaches.
What can we do to prevent ransomware attacks?
Here we list some practices to reduce the risks of ransomware attack:
- Do regular back up and store them in secure places, as for example, Cloud applications.
- Upgrade your OS systems and pay attention to the latest security patches.
- Avoid using OS cracked versions.
- Close your ports 445, 135, 137, 138, 139.
- Install a powerful combination of antivirus + antimalware in all your networks, and make it extensive to every device with access to them.
- Corroborate the source of your emails and internal communications, and; as general practice, disregard and avoid opening attachment or link from unknown sources.
Our expert speaks out

Daniel González, our expert in Security issues, enlighten us about the options we have to potentiate our systems and shield them against ransomware attacks.
As previously expressed, this ransomware exploits a vulnerability in the SMB protocol to spread out in the networks. This attack made evident the underlaying inadequacy that most companies have to manage their security protocols in order to keep pace with patches and upgrades delivered by manufacturers.
With the purpose of helping us with our Vulnerability Control and Vulnerability Inventory, we count on Nessus. We can verify through its own plugins all available patches and vulnerabilities to keep updated our vulnerability inventory.
By the same token, it’s pretty clear that keeping pace the security patches can be really difficult. In this regard, we move into the difficult terrain of Business Availability vs. Implementing Security Changes in Production Environments. Important to highlight; in this contest it usually wins business availability.
In order to give solution to this issue, TrendMicro offers Deep Security. This tool allow us to make real-time virtual patches in the server; without interrupting your services. Also; TrendMicro offers TippingPoint, which is an IPS solution to protect our assets in real time by blocking packages with malicious patterns.
SIEM
SIEM solutions allow us to have full insight in real-time about our services and application via log event and log correlation management. Alienvault is one of the most complete SIEMs available on the market; with multiple mechanisms of protection that help us to prevent ransomware attacks.
AlienVault counts with a vulnerability analysis engine and patch control (OPENVAS) that enables us to have information about our network’s inventory. Also, it counts on rules for data cross-correlation to verify if our networks are currently exposed to vulnerabilities; while receiving logs if any attack strikes our platforms.
With this purpose, AlienVault raises alarms in our systems and send them to our emails; and/or executes immediate actions to stop the attack. Additionally, it counts with HIDS (IDS Hosts) y NIDS (Network IDS) to verify what’s going on in our hosts and networks.
So, how much does Ransomware WannaCry cost? What are your options to protect your company?
To give answer in monetary terms about how much has it costed the ransomware WannaCry to the affected companies; simply do the math: More than 20,000 enterprises reported the ransomware attack only in Colombia; and each rescue asks for around 300 bitcoins. The equivalence is USD 1.00 = BTC 0.0006.
However, the highest cost goes beyond money: The affected enterprises have to disconnect their devices from their networks; and instructed their employees to do the same with their personal devices. Additionally, we prevent mass lay-offs and work team reconfigurations as spin off process. Besides, among the costs, we need to take into account the necessity of totally upgrading the security platforms, protocols and good practices in security systems.
Avoid that this scenario knocks at your doors. Discover our tools to leverage your digital security while comprehensively protecting your assets from ransomware attacks.
—-
1. Source in Spanish.
2. Source in Spanish. Translated by GB Advisors, Inc.



